IntroductionPrevention of security vulnerabilities is increasingly important as new threats and defenses are discovered. In order to support your asset protection, ATEasy includes many security features in compliance with DOD Application Security and Development (ASD) and DISA Security Technical Implementation Guide (STIG). ATEasy is compliant with ASD version 4 release 10 (V4R10) released October 25, 2019 (293 requirements).
For example, the following audit requirements met by ATEasy:- Start/End session/program
- User modifications and login/logoff
- Inactivity locked timeout
- Password policy: term, repeats, disabled accounts, format (# of characters, upper lower/numeric, signs…)
- User file protection and read-only setup
Throughout your product's lifecycle, ATEasy provides encryption and a user administration interface to increase application security from conception to operation. |
|
ATEasy User AuditingMany attack vectors exploit improperly administrator user privileges. To mitigate the risks stemming from poorly defined user rights, rigorous user account management includes auditing. In addition to any enterprise-level solution, ATEasy also features user auditing. When enabled, ATEasy will generate audit records in Windows Event Log for the following events and their event ID number:
Audit Start/Stop - records to ATEasy Windows Application Event Log- ATEasy or Application Start (1010)
- ATEasy or Application Exit (1011)
Audit User Log In/Off - records to the ATEasy Windows Application Event Log- User Login Succeeded (1020)
Audit User Modifications- records to the ATEasy Windows Application Event Log- User Password Change Succeeded (1030)
- User Password Change Failed (1031)
- User's File Replaced (1035)
- User's File Changed (1036)
Auditing establishes self-audits adding to existing security standards and best practices. User action traceability is a key security feature. Figure 1 shows an example of Windows Event Viewer and ATEasy audits. The log provides information security personnel an easy way of tracing user interaction.
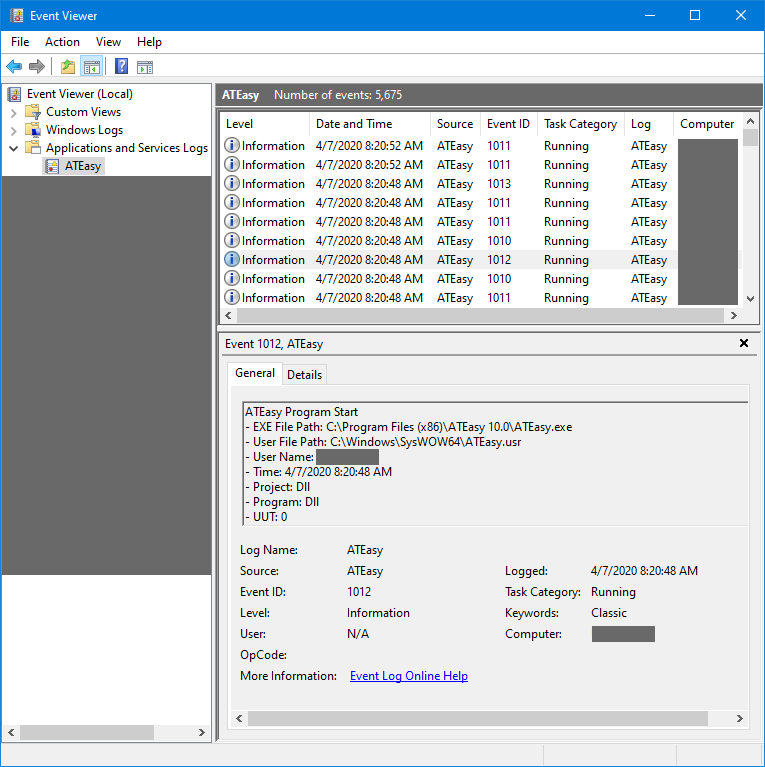 Figure 1. ATEasy logs application events, viewed here with Windows Event Viewer.
Building Safe ATEasy ProjectsAll user data is encrypted by default to prevent unauthorized access. Common application security flaws include revealing too much information about error conditions for example in the form of stack traces, detailed network timeout errors, buffer overflows and database structures. To support secure development through proper error handling, ATEasy has built-in support for example:- Try-Catch blocks to localize the handling of exceptions
- OnError() module events to catch all / ease handling of runtime errors
- Error statements in user code to generate error conditions allowing centralized or grouped error handling (OnError /Try-Catch)
- Procedures to process unhandled exception
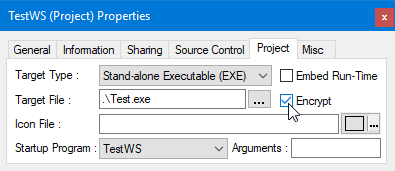 Figure 2. Encrypting Executables is Accomplished by Checking Encrypt
Projects can be built into an executable or DLL. Figure 2 shows ATEasy project properties with secure options available. Embedding runtime library can help prevent loading malicious libraries in man-in-the-middle/API-hooking attacks. In particular, when 'Encrypt' is checked the executable or DLL created receives a digital signature with its PCode section encrypted. This feature guards project integrity against file corruption or malicious changes. If the created EXE or DLL file is encrypted, it cannot be read for example using a text viewer. Figure 3 shows File Encryption being enabled for a Program module.
Benefits of project target encryption include:- Maintain executable integrity and prevent hacking or modifying executable (Non-Repudiation)
- Prevent reverse engineering and PCode code viewing
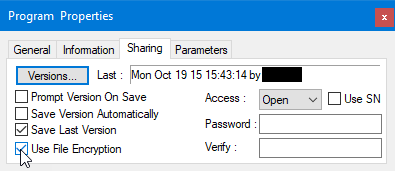 Figure 3. An administrator can set passwords for modules to control access
Secure ATEasy RuntimeATEasy includes features like stack overflow and mismatch checking to maintain project integrity. Buffer overflow protection prevents exploits that utilize malformed input injections. ATEasy implements Control-Flow Integrity to prevent stack smashing and injection of malicious code. Runtime applications are secured and provided with encryption. Binary source code encryption has many benefits. ATEasy verifies files as they are opened which contributes to protection from malicious changes.
The benefits of using password or license serial number protection cannot be reiterated enough. Using access control protects applications from using, viewing, editing and reverse engineering of code by potentially harmful actors. In addition to access control, ATEasy also provides automatic file versioning. Versioning also provides additional recordkeeping capabilities.
ATEasy User Administration, Access Control and VersioningAccess control throughout project lifecycle is paramount for application security. ATEasy includes many features for robust user administration.
Administrator can specify access level and password. Alternatively, ATEasy serial number can be used to grant access based on license. In addition to controlling access, user changes to project files can be subject to versioning. Each version of project files can be labeled and time stamped promoting further tracing of changes and user actions. Figure 4 shows an example project using automatic versioning.
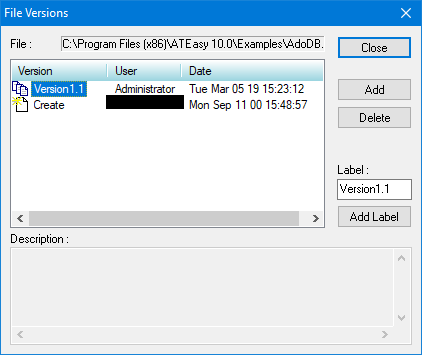 Figure 4. Tracking versions is convenient with periodic auto save enabled.
User interaction can be limited to selecting and running tests with short menus. User login maybe required with ATEasy launch with Use Login Dialogbox. Minimum password length can be enforced as well. ATEasy users can be granted rights as individuals and as group members. Custom groups can be created and user rights can also be set/read in AUser class. These user rights are detailed in figure 5, while figure 6 shows how intuitive enforcing ATEasy information security can be.
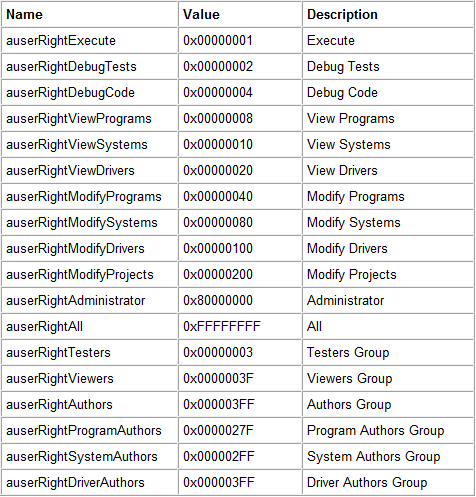 Figure 5. Given proper clearance, user rights can be set from Users menu as well as in an instance of AUser class.
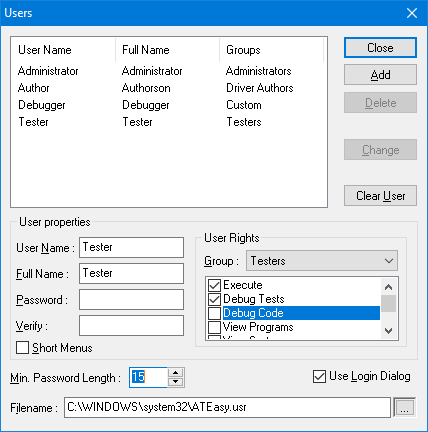 Figure 6. Access to the IDE can be made selective based upon group definition.
Test Executive User Administrator, Access Control and VersioningIn addition to ATEasy, Test Executive also contains tools for configuring user rights and access to your application's functions. Administrator can hide/show/enable/disable/rearrange commands, menu items, toolbar & form buttons, and options to handle customization privileges and access to test executive features. An administrator can add and modify available user groups as shown in figure 7, while figure 8 shows a menu for modifying group users.
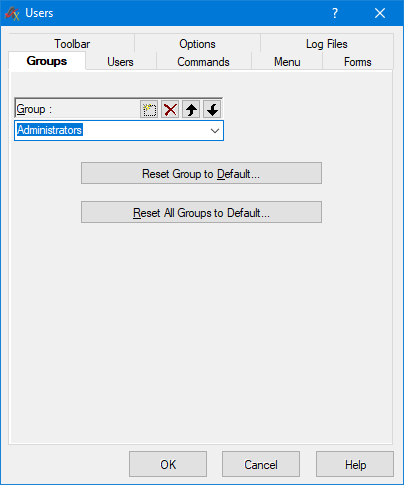 Figure 7. Group changes can be made
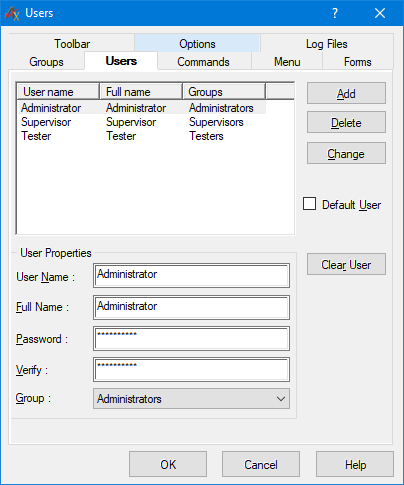 Figure 8. Users can be modified.
Commands available to a Test Executive user can be restricted to based on individual or group settings. Each command can be mapped to custom procedures. For example in figure 9, changing a password is disabled for user group Testers. Much like commands Test Executive's available menus items can be restricted based on user privileges. An example of menu item customization is seen in figure 10, where access and organization of the Testers group menu is considered.
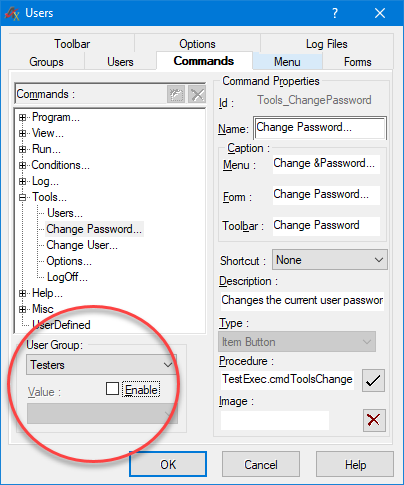 Figure 9. Group specific restrictions can be applied by disallowing functionality for specified parameters
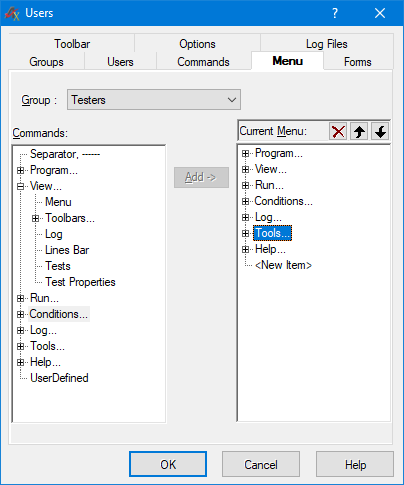 Figure 10. Menu items can be restricted as well.
Application toolbars and options are also available for customization according to user access level. Control of available options can restrict use of for example user being able to delete log files. In figure 11 example, the Test Executive toolbar seen by Supervisors group is being modified.
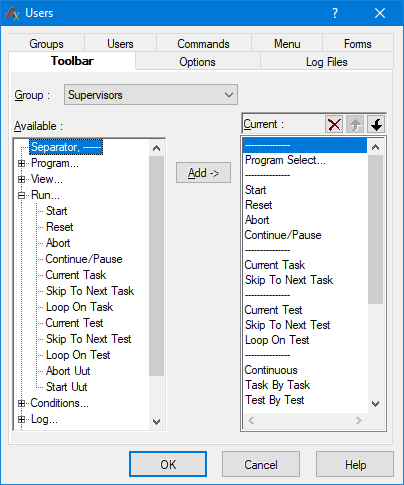 Figure 11. Setting a custom toolbar for the Supervisor group
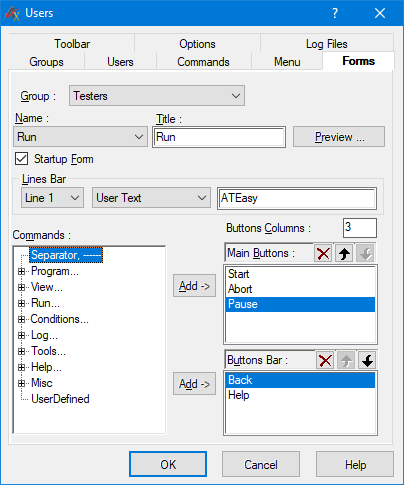 Figure 12. Specifying modal user interface for a given group name
Figure 12 shows configuration of the Test Executive touch panel user interface in the case Testers user group. Access to commands linked to form items can be added and removed from user group. Additionally, figures 13 and 14 show more user interface options that can be set for a given user groups and modal and modeless dialog. In figure 13 for example, whether window is shown in full screen can be set. Figure 14 shows some example groups and how their user password minimum requirements can be mandated.
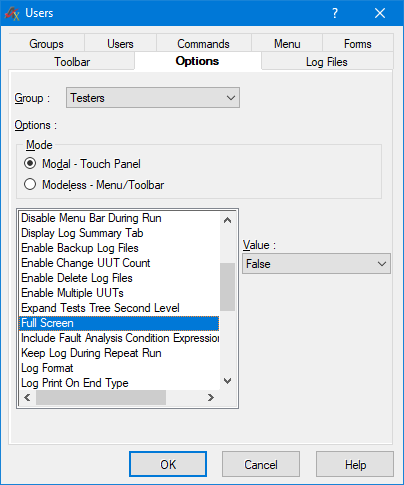 Figure 13. Customizing options for the group Testers
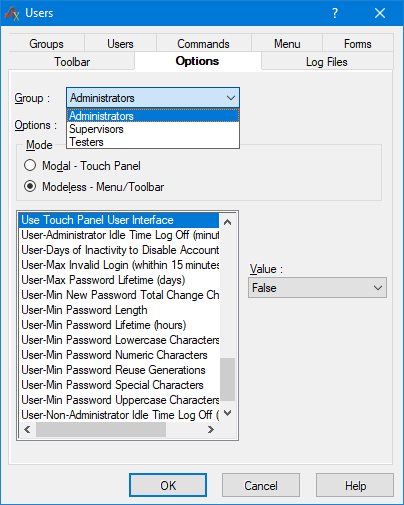 Figure 14. Customizing options for the group Testers
ConclusionATEasy and Test Executive provide STIG V4R10 compliant, as well as many other, tools for secure application development. ATEasy applications are deployed across many different platforms and can have a long lifetime, in which case the usefulness of ATEasy built-in application security capabilities will likely only increase with time.
[References]
https://stigviewer.com/stig/application_security_a
|
|
Keywords
|
STIG,ATEasy,cyber,security,hacking,executable,integrity,DoD,DISA,exploit, ASD, V4R10
|